A Self-Sovereign Digital Identity
Close to a billion people worldwide currently have no form of legal identity. Simply put, an identity card enables a person to access the majority of the economy and better their circumstances. Behind this lack of digital identity is significant amounts of locked economic value. Without a standard identity, a person’s access to everything from banking, loans, and business ownership to housing, healthcare, and education is severely limited.
According to a 2019 Mckinsey study, full identity coverage, specifically digital identity coverage, would allow for the economic value of between 3%-13% of GDP to be unlocked. 3%-13% of a nation’s GDP totals billions of dollars. Here lies not only an incentive based on humanitarian terms but economic terms. A study conducted by Juniper Research claims that the revenue for digital identity vendors will jump from $26 billion in 2021 to $53 billion in 2026. The next frontier of the distributed economy is the digital identity solution, whoever solves this problem will be the next unicorn.
As the transition between a centralised oligarchical Web 2.0 system pushes toward a decentralised and distributed Web 3.0 infrastructure, user-controlled identity verification becomes more critical. The keyword to emphasise here is user-controlled. Personal choice is the foundation of the digital economy. The balance of power is shifting away from the large technology corporations to the individual. As such, the digital identity infrastructures must represent and facilitate this change. Individuals now must have a form of digital identity, but specifically, own their digital identity and remain in charge of it. Users must have the right to share or not share their personal information with third parties and have the tools to control how their information and data may be used.
In a world where digital identity fraud is a common concern, users need to ensure that their information is not sitting around on open servers, waiting for the next data leak to compromise their personal data. Therefore, we understand that the industry needs to emphasize solutions that create practical digital identities and controls so as to give control to the individuals. To ensure that security mechanisms are sufficient to protect both information and choices, selections and transactions. The end-user should be the only party with access to the data, with no compromises.
The concept of personal choice is of utmost importance. Our philosophy is to take a holistic birds-eye view of personal choice, allowing individuals to control their digital lives, Whatsoever they may be. That’s why we are Nest®.
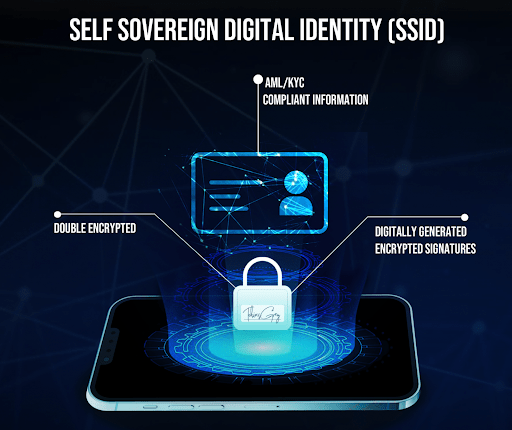
This control begins with creating an SSID or a Self-Sovereign Digital Identity. At the beginning of our user experience, individuals can choose to register their credentials, and the ecosystem generates a dynamic data asset; think of a hyper-encrypted, living blockchain-element. This asset is minted on our Layer 1 solution, and the complete asset sits in our omni-network, double-encrypted wallet and storage service. A hyper-encrypted, decentralized Content Delivery Network [CDN], if you prefer. The users are the only ones with access to their own information. This information is splintered into multiple pieces, encrypted and stored across various nodes to aid speed and available sources of retrieval, say as in the case of a lost account access. It is the one user that holds the only key to decrypt their information.
–
–
Alongside this dynamic data asset, systems generate digitally encrypted signatures that permit approving actions, like data exchange or provenance or registrations. These follow Zero-Knowledge-Proof [ZKP], protocols. NEST® digital signatures are further used to share personal information, transfer the SSID across protocols for participation, and engage in the truly digital distributed economy.
Our approach recognizes three pillars to the future of digital identity. The first pillar is a representative, self-defined and owned digital identity. The second is adequate security mechanisms to protect the storage and use of this digital identity. The third is the right for personal choice. At NEST®, we understand that no one pillar can be ignored or omitted. The purpose of our solutions is to enable the user-led control of one’s own economic potential. Using our SSID, users can take charge of monetizing their own data, and unlock economic value once reserved for the large corporations. Your data – your choice. This is our core.
–
Aman Deol
http://NES.TECH/









