You scroll through Facebook aimlessly when one day a certain suggestion catches your eye. They’ve got a vaguely familiar surname but aren’t connected to anyone in your circle. So, you do a little digging only to find that they’re an estranged family member.
Sounds like a bit of a stretch?
Unfortunately, it’s not. This was how Kashmir Hill discovered their long-lost relatives. Although they had a sweet reunion, Facebook’s omniscience concerned them. You may think that you shouldn’t be too concerned since all companies hoard data, and this is only just to show freakishly accurate ads. Sadly, you’re mistaken.
NEST® reveals how, in a Web 2.0 setting, companies and governments use your personal data and gives its take on how Web3, the new version of the internet, will change how data is handled.
Web 2.0 Has Tossed Us Into An Orwellian Nightmare

In the classic novel 1984, the ruling party keeps its citizens in check with mass surveillance and spreads propaganda to brainwash them into submission. Freedom of expression and thought is non-existent, and anyone who crosses the line is persecuted.
Can Web 2.0 be heading in this dystopian direction? It’s possible.
Mass Social Media Surveillance
Governments across the world are instituting advanced surveillance programs in the name of enhancing security, limiting disinformation, and ensuring public order. But is this for the greater good, or is there a more sinister agenda at play?
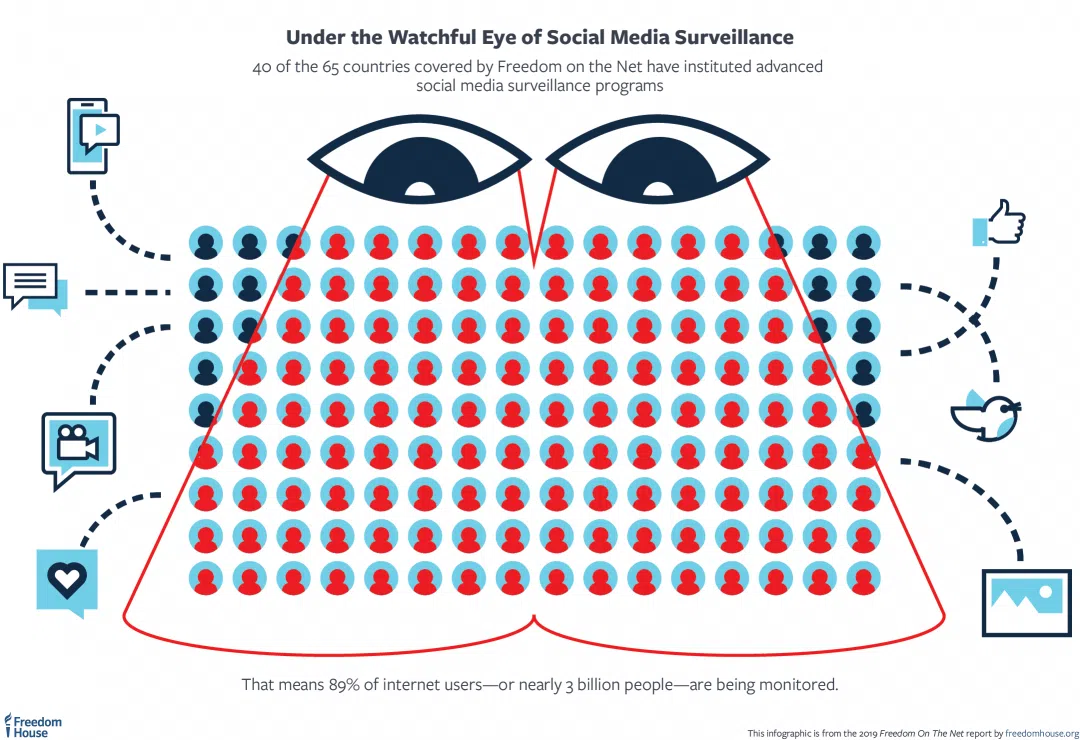
According to a 2019 report from Freedom Net, 40 of 65 countries researched use surveillance programs. This accounts for more than 89% of the internet population, which means governments around the world now monitor more than 3 billion people who are online.
Currently, China is leading in the manufacturing and exporting of mass surveillance tools that can provide a “full view of the virtual world and analyze unlimited data”.
What does that mean?
Surveillance tools can analyze millions of posts and user interaction and instantly break or bypass the encryption on your messages. This means governments can analyze, record, and scrutinize even the text messages you send in private. Such data collection happens even when you’re not using the application frequently, so once it has been installed on your device, there’s generally no way to avoid this type of surveillance.
The worst part is that regressive nations are using these tools to stifle multiple forms of expression, as well as actively discriminating against select groups or minorities. So, mass surveillance is becoming the very human rights problem global networks and user-held technologies first sought to mitigate.
Security Threats From Centralization
Google’s products and services have more than 1 billion users worldwide and social media platforms like Facebook have more than 2 billion active users every month.
Collected data is typically stored on companies’ centralized servers. This is a major security concern, as a single attack on these servers can potentially expose the data of millions of users and adversely affect online businesses.
The most recent example is Facebook’s 2021 data breach, in which hackers scraped the data of some 533 million individuals from its servers. While it remains unclear what the hackers intend to do with the data, more than half a billion users had their credentials exposed.
It’s suspected the hackers aimed to use it for social engineering attacks, in which the attacker coaxes the targeted individual to then divulge sensitive and personal information, by pretending to be someone they know and trust.
So, if you think your data is worthless, think again. There’s a high chance you or someone close to you may end up a victim in these or similar types of attacks on centralized repositories.
Data Exploitation And Large-Scale Manipulation
In “1984,” the ruling party changes records and twists information to brainwash citizens into thinking they were moving toward the future when, in reality, the country was stricken with poverty.
In the book, this misdirection and manipulation were called ‘doublethink’, and if you look closely at Web 2.0 trends, there are many instances where data was exploited to influence people’s opinions in a similar manner or for generally identical purposes.
A notable recent incident was the infamous Cambridge Analytica scandal, in which 87 million users’ data was exploited and used to influence the 2016 U.S. Presidential elections in Donald Trump’s favor.
Recently, China joined the doublethink bandwagon and U.S. Secretary of State Antony Blinken expressed concern over the country’s misuse of free media to spread pro-Beijing propaganda. This is to say nothing of the ongoing Russian propaganda machine working to present the ‘liberation’ of Ukraine as a worthwhile, noble goal.
In these and other instances, organizations first use personal data to determine user preferences and then precisely target them with tailored, influential, content determined to potentially change their minds and/or reinforce what they would have them believe.
Sounds exactly like ‘doublethink’, doesn’t it?
Yes, but all these incidents sound more like a government problem and less like a problem with the internet.
So, What Role Does Web 2.0 Play?
Mark Andrejevic, professor of media studies at Monash University and an avid critic of surveillance, calls the internet “an interactive realm wherein every action and transaction generates information about itself,” creating opportunities for loss of privacy and mass surveillance.
In other words, it’s the key features of the internet itself that offer more visibility and information to organizations and governments.
For example, if you visit a website, advertisers may leave third-party cookies to identify your shopping preferences and give you a more “personalized” user experience.
If you create a social media profile, the platform will track your political preferences, sexual orientation, occupation, connections, and other personal details based on or derived from the content you create and consume.
Right now, I’m using Google Docs to type this article and every word I type is sent to the company’s servers. I can only assume that Google won’t use this data for other purposes based on its advertised privacy terms. Yet, I still can’t be sure that Google, at any time, will have the power or authorization to change such privacy terms as they deem fit.
So, every click in Web2 is data input that’s fed to massive databases that can be hacked or used by some central authority to monitor your online activity.
That sounds scary. But do we have a way out?
Enter Web3, The Decentralized Network Of The Internet

Differences between web2 and web3 are vast. Web3 is built on distributed ledger technology – blockchain technology being the most commonly known variation, and allows the next iteration of the internet to be a paradigm shift in how companies are able to handle their customers’ data. In other words, when executed correctly, Web3 is structured in a way that gives back control to users and reverts them to autonomous ‘consumers’.
Since neither tech giants nor individual users monopolize the internet, online communities, as well as organizations, are incentivized to take part in Web3’s development and maintenance. This newly enacted autonomous control and immutable accounting allow content creators and user-generated content to authentically thrive.
Rather than centralized repositories in Web2, Web3 decentralized protocols are now able to store your data and files. In other words, a bunch of computers now store your data instead of centralized servers. That way, any one individual location or organization is not wholly susceptible to hacking, and any one company will not be in the same control to sell your data.
When correctly enacted, there is no one central authority or government which can access your data, as Web3 enables the creation and control of self-sovereign identities giving you decisional power over who and how you share your data.
What’s that now?
Think of a self-sovereign identity as an unbreakable briefcase you alone hold, which also contains any data you would like it to contain. You don’t have to open this briefcase for anyone else apart from yourself, even when using the content of that briefcase for verification. Content inside can already be verified by trusted authorities, as you select.
With this briefcase in hand, authorities can check only their identified or selected verifier’s authenticity and not the entire content of your case – for instance, when verification is needed for access or transactions on any Web3 network. For instance, if you want to show age proof in a casino, you can do that without revealing any other personal or identifiable information during that exchange. Apart from your age, nothing else is revealed or confirmed.
This protected form of ownership control means you can remain truly anonymous online and, should you wish, post honest opinions without worrying about being doxed or arrested. This alone is an enormous shift for those living in highly restrictive jurisdictions.
Web3 eliminates most requirements for middlemen, those sitting in-between the user and service during online engagements or transactions. It allows autonomously secured individuals to interact with each other directly. In this environment, Facebook, for example, cannot be in a position to take down your posts, Google can’t remove your app from the Play Store, and governments can no longer ban particular apps or websites in the Web3 space.
In short, thanks to DLT, Web3 has the potential to give users tangible and trusted control over both their data and identity. It’s still a work in progress, so its current iteration does indeed have some drawbacks.
Web3 Drawbacks
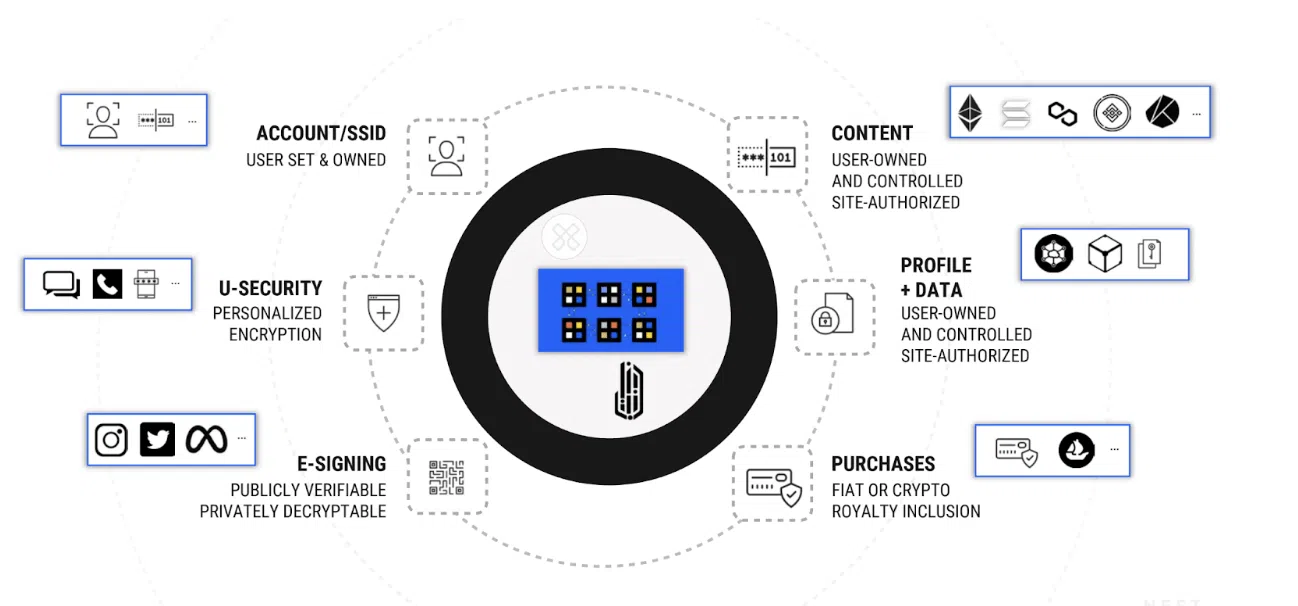
Here are some of the most common Web3 drawbacks and how NEST® is solving them:
- It’s hard to prove ownership over digital assets: Unlike in the real world, where you have multiple means to prove ownership over real-world assets (for example, a physical ID issued by a central authority alongside a sales receipt), the Web3 world doesn’t have a broadly accepted or ‘standard’ protocol for concrete ways to establish ownership. This is partially due to its pseudo-anonymous nature.
NEST® ‘s Distributed Ledger Technology (DLT) creates a self-sovereign distributed ID (SSDID)which helps you create and exchange assets with a digital stamp that’s unique to you. This way, you can prove your identity online without compromising your genuine anonymity and, functioning as a notary service, also execute smart contracts safely.
- It’s not possible to prove the authenticity of a digital asset: The real world has tests to determine an artwork’s authenticity. But if you’re buying digital assets like NFTs online, there’s currently no way to truly verify their authenticity.
NEST® can run copyright checks to ensure you’re not buying a plagiarized or stolen piece. If you’re an artist, NEST® can lock your assets with your personal encryption, instead of hosting them on open servers. Now you are in charge of an authenticated, personally controlled asset that cannot be stolen and re-minted.
- Web3 isn’t interoperable: If you’re currently using MetaMask, you need a third-party like Chainlist or to input data manually so as to connect it to another blockchain network. Current blockchains operate as individual ecosystems and typically do not allow for real interoperability. For example, your Ethereum account cannot give you access to Solana nor could it fund the execution of transactions anywhere else.
However, the NEST® ecosystem has already solved the problem. You can create your self-sovereign ownership controls, digital assets, and exchanges directly and simply select which network you wish to execute these on – all with just a few clicks through your mobile device.
Wrapping Up
Web2 has somewhat ended up stripping away the potential right for user privacy and freedom of expression. This comes from its centralized nature.
Governments and other third-party organizations today have almost free reign over the unlimited data most sites and social networks provide. Sadly, this hyper-vigilance is pushing us towards a dystopian setup.
Web3 is a new, DLT-powered iteration of the internet that holds the real potential to give back users control of their data and online identities. It allows them to express their opinions freely, securely transact, or exchange as they decide and choose who or how others can access their data.
In this context and position, Web3 is undoubtedly superior to Web2 – particularly in terms of privacy. But it still has a long way to go in terms of scalability, awareness, and adoption.
If you’re ready to join the Web3 revolution and ensure your confidential ownership control using next-gen digital asset authentication, follow NEST® on Twitter and Medium.