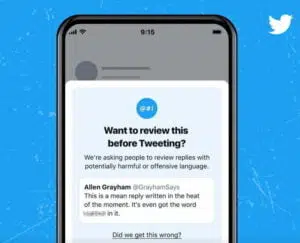
TWITTER CHECKING LANGUAGE
Distributed ledger technologies (DLT) require a peer-to-peer network and so-called consensus algorithms to ensure that data is replicated across all nodes...
A NOTE ON TELEGRAM
True or Genuine End-to-End Encryption (G-E2EE), is attained when the hosting application does not have access to the users' exchanged content. If this definition of G-E2EE is accepted, the
What Is Distributed Ledger Technology (DLT)?
Distributed ledger technologies (DLT) require a peer-to-peer network and so-called consensus algorithms to ensure that data is replicated across all nodes...
Smart Contracts and Their Potential and Inherent Limitations
“Smart contracts” are a critical component of many platforms and applications being built using blockchain or distributed ledger technology. Below, we outline the background and functi
The Truth About Blockchain
“Contracts, transactions, and the records of them are among the defining structures in our economic, legal, and political systems. They protect assets and set organizational boundar
What is a blockchain oracle?
“Blockchain oracles are third-party services that provide smart contracts with external information. They serve as bridges between blockchains and the outside world. Blockchains
A systematic literature review of blockchain cyber security
Abstract “Since the publication of Satoshi Nakamoto’s white paper on Bitcoin in 2008, blockchain has (slowly) become one of the most frequently discussed methods for securing
Microservices Architecture
“Over the past few years enterprises and industry leaders have been steadily adopting microservices to drive their business forward. At this point, companies like Amazon, and Googl
Salting, Hashing, and PBKDF2
Passwords are very private information, and you don’t want to be responsible for a data breach. You should take the highest precautions if you have to handle them in your application, an
What is webRTC
“WebRTC stands for Web Real-Time Communication. It’s a low-latency technology that uses JavaScript APIs to access your computer’s camera and microphone, thereby enabling media t