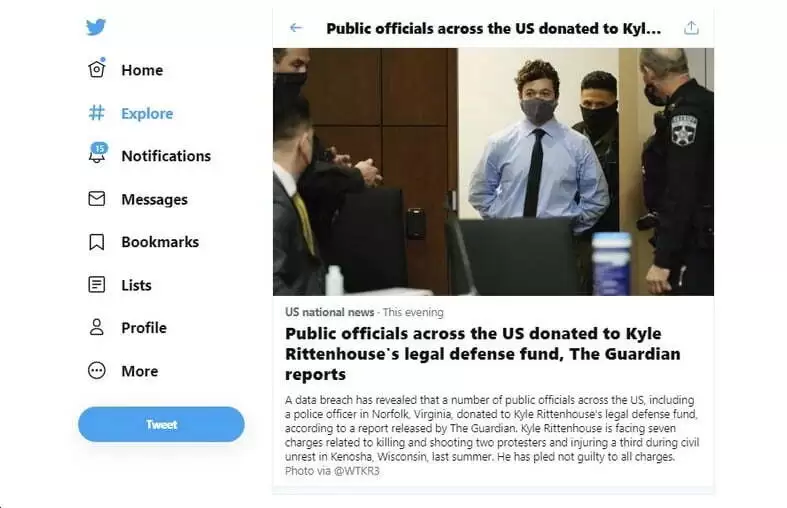
TWITTER REPORTS
"... but that all seems to depend on who’s being hacked and doxxed. Reports now talk about the UK’s Guardian newspaper running a story, apparently based on material trafficked by hacke
FB 2021 DATA LEAK
Distributed ledger technologies (DLT) require a peer-to-peer network and so-called consensus algorithms to ensure that data is replicated across all nodes...
What is zero trust?
A zero-trust model is a security framework that fortifies the enterprise by removing implicit trust...
The Death of Freedom by Software
Distributed ledger technologies (DLT) require a peer-to-peer network and so-called consensus algorithms to ensure that data is replicated across all nodes...
Twitch plays internet police
Distributed ledger technologies (DLT) require a peer-to-peer network and so-called consensus algorithms to ensure that data is replicated across all nodes...
A NOTE ON TELEGRAM
True or Genuine End-to-End Encryption (G-E2EE), is attained when the hosting application does not have access to the users' exchanged content. If this definition of G-E2EE is accepted, the
RSA ENCRYPTION
RSA encryption is a system that solves what was once one of the biggest problems in cryptography: How can you send someone a coded message without having an opportunity to previously sha
What is a blockchain oracle?
“Blockchain oracles are third-party services that provide smart contracts with external information. They serve as bridges between blockchains and the outside world. Blockchains
PGP ENCRYPTION
If you use PGP encryption tools in the correct way... it can offer military-grade data security.
Salting, Hashing, and PBKDF2
Passwords are very private information, and you don’t want to be responsible for a data breach. You should take the highest precautions if you have to handle them in your application, an